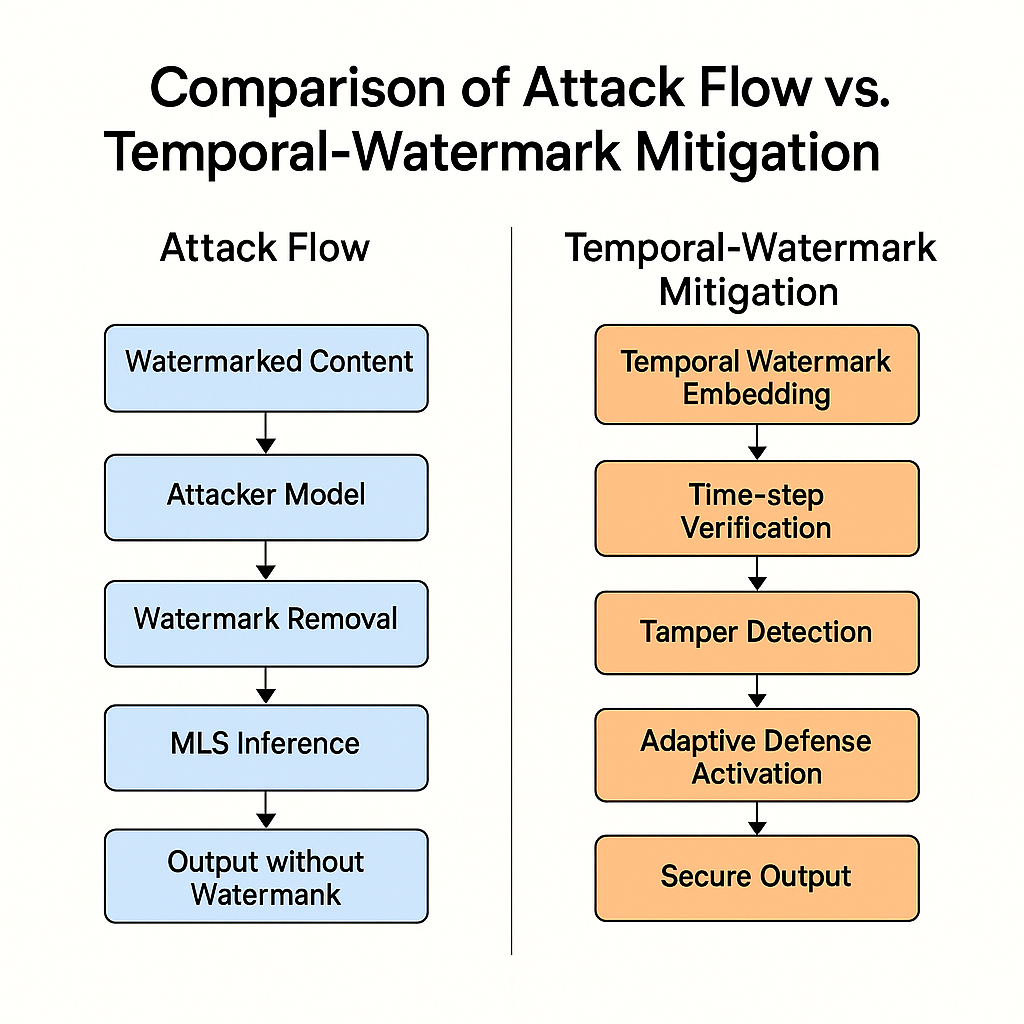
The MGM Breach Didn’t Break In — It Logged In
The MGM breach didn’t start with malware or a zero-day. It started with trust. This article breaks down how identity, help desk workflows, and routine access decisions created the real attack path-and why modern breaches increasingly “log in” instead of breaking in.






%201.webp)